 accesses since July 1, 2004
accesses since July 1, 2004 copyright notice
copyright notice
 link to published version: Communications of the ACM, September, 2004
link to published version: Communications of the ACM, September, 2004
 accesses since July 1, 2004
accesses since July 1, 2004Hal Berghel
While the fact that WiFi technology has a few security vulnerabilities is not news, the extent of these vulnerabilities may be surprising. In this column, we provide one such exemplar: War Driving.
WIRELESS-IN-A-NUTSHELL
The concept of wireless networking dates back at least as far as ALOHANET in 1970. While this project is now of primarily historical interest, the online overview is still worth reading (http://en.wikipedia.org/wiki/ALOHA_network). The concept of ALOHANET spanned many of the core network protocols in use today, including Ethernet and Wireless Fidelity (aka WiFi ®). ALOHANET was the precursor of first generation wireless networks.
Wireless technologies may be categorized in a variety of ways depending on their function, frequencies, bandwidth, communication protocols involved, and level of sophistication (i.e., 1 st through 3 rd generation wireless systems). For our purposes, we’ll lump them into four basic categories: (1) Wireless Data Networks (WDNs), (2) Personal Area Networks (PANS), (3) Wireless Local Area Networks (WLANs), of which the newer Wireless Metropolitan Area Networks (WMANs) and Wireless Wide Area Networks (WWANs) are offshoots, and (4) satellite networks.
WDN is a cluster of technologies primarily related to, developed for, and marketed by vendors in the telephony and handheld market. This market covers a lot of ground from basic digital cellular phones to relatively sophisticated PDAs and tablet PCs that may rival notebook computers in capabilities. WDN includes protocols such as the Cellular Digital Packet Data (CDPD), an older 19.2Kbps wireless technology that is still in use in some police departments for network communication with patrol cars; General Packet Radio Service (GPRS) and Code Division Multiple Access 2000 (CDMA2000) which are multi-user, combined voice and data 2.5 generation technologies that exceed 100Kbps; and Wireless Application Protocol (WAP) which provides wireless support of the TCP/IP protocol suite and now provides native support of HTTP and HTML. If you’re using a cellular phone with text messaging and Web support, you’re likely using some form of WAP.
PANs began as “workspace networks.” Bluetooth, for example, is a desktop mobility PAN that was designed to support cable-free communication between computers and peripherals. Blackberry (www.blackberry.com) is like Bluetooth on steroids. It integrates telephony, web browsing, email, and messaging services with PDA productivity applications. As such it blurs the distinction between PAN and WLAN.
WLAN is what most of us think of Wireless technology. It includes the now-ubiquitous 802.11 family of protocols, as well as a few others. Table 1 provides a quick overview of some of the 802.11 protocol space. Note that all but the first are derivative from the original 802.11 protocol introduced in 1997.
TABLE 1: THE 802.11 PROTOCOL FAMILY
| Standard | 802.11 | 802.11a | 802.11b | 802.11g | 802.11n |
| Year | 1997 | 1999 | 1999 | 2003 | 2005 |
| Frequency | 2.4GHz | 5GHz | 2.4GHz | 2.4GHz | 5GHz? |
| Band | ISM | UNII | ISM | ISM | ? |
| Bandwidth | 2Mbps | 54Mbps | 11Mbps | 54Mbps | 100+Mbps |
| Encoding Techniques | DSSS/ FHSS | OFDM | DSSS | OFDM | ? |
n.b. “Year” denotes approximate year of introduction as a standard (e.g., 802.11a and 802.11b were introduced at the same time, though 802.11a came to market later). The two bands used for “WiFi” are Industrial, Scientific and Medical (ISM) and Unlicensed National Information Infrastructure (UNII). Bandwidth is advertised maximum. Encoding, aka “spectrum spreading” techniques appear at the physical or link layer and include frequency-hopping spread-spectrum (HPSS), direct-sequence spread-spectrum (DSSS), and orthogonal frequency division multiplexing (OFDM).
We note in passing that both the 802 and 802.11 landscape is somewhat more cluttered than our table suggests. For example, 802 also allows for infrared support at the physical layer. In addition, proprietary standards for 802.11 have been proposed. In 2001 Texas Instruments proposed a 22Mbps variation of 802.11b called “b+”, and Atheros proposed a 108Mbps variant of 802.11g called “Super G”. Further, there are standards for enhanced QoS (802.11e) and enhanced security (802.11i) that are actually orthogonal to the traditional 802.11 family in the sense that they deal with limitations rather than the characteristics of the protocol suite. To make comparisons even more confusing, there are 802.1x protocols like 802.16 (2001), 802.16a (2003) that are designed for wider area coverage, the so-called “Metropolitan Area Networks” or MANs. The 802.11n specifications are thin as of this writing, although the current attention is on increasing throughput at the MAC interface rather than the physical layer.
THE ORIGINS OF WAR DRIVING
Rumor has it that the concept of “War Driving” was first formalized by Peter Shipley sometime around 1999. His early War Driving experimentation was subsequently introduced to the wider hacker community at DEFCON 9 in Las Vegas in July, 2001 Figure 1 was derived from this experiment.
The basic idea behind War Driving is to “sniff” 802.11 traffic with a wireless card set in “monitor” mode so that it accepts all traffic on frequency irrespective of intended target. War Driving is an extension of the concept of War Dialing that deserves some explanation.
Figure 1: An Early WAP Map- circa 2001.
(source: Peter Shipley: “Open WLANs – the early results of WarDriving,” http://www.dis.org/filez/openlans.pdf)
War Dialing is the technique that the main character in War Games uses to gain access to computer systems. One might recall that in an effort to access computers of a computer game company, the character inadvertently launched a nuclear war. Though modem banks are technological dinosaurs, they remain in use and are one of the easiest network appliances to compromise.
War Dialing is the art of scanning lists of phone numbers for the carrier tones that betray modem lines. The target lists are derived from sundry public-domain sources such as telephone directories (e.c., 411.com), WHOIS domain registration Websites such as Internic (www.internic.net/whois.html), contact information on organizational Websites, and so forth. The principle is pretty simple: find an organizational telephone number, and then sweep through the range of numbers that includes it for the presence of a modem. A modem’s carrier tone signifies a receptive appliance, so the War Dialer records a “hit”. A suitably enhanced War Dialer can “nudge” the unsuspecting modem line to try to produce a logon prompt, and then to produce an acceptable logon sequence. A Web search will confirm that War Dialers in both shareware and commercial versions abound for both Windows (e.g. THC-Scan 2.0) and *nix (e.g., Ward) platforms. At one point, the good folks at l0pht.com even produced a Palm-based War Dialer called TBA (c.f., www.securiteam.com/tools/TBA_-_PalmOS_wardialer.html).
WARDRIVING TAKES SHAPE
There is no question that there is a legitimate, lawful use of War Dialing – to determine whether there are insecure modems connected to one’s own network. Of course, this knowledge is also of use to potential intruders.
Similarly, War Driving is the art of monitoring wireless traffic. The legitimate, lawful use is to control signal strength, bandwidth, leakage patterns and so forth for one’s own wireless environment. And again, this information is useful to potential intruders.
One thing that distinguishes War Driving (aka, WAP mapping, and transportation-centric offshoots like War Walking, War Biking, War Flying, War Boating, and the like) is that they all relate to the various modes of mobile sniffing of wireless traffic. Generally speaking, if the sniffing is used in support of the owner/organization’s interests, the use of less alarming euphemisms like “wireless monitoring” or “vulnerability testing” is encouraged.
But, let’s be real. War Driving surpasses wireless monitoring by a large measure. To wit, the War Drivers have even created their own brand of War Driving signage called War Chalking (Figure 2) that reveals such tidbits as whether the service set id, bandwidth and whether security is enabled. The War Chalker identifies the characteristics of the unwitting target on the most convenient concrete surface in much the same way that the Hobo Chalkers did during the depression (see references).
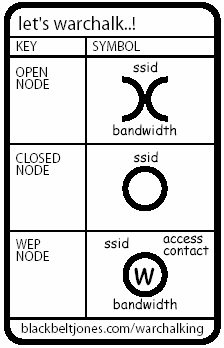
Figure 2: A War Chalker Card (source: blackbeltjones.com)
In addition, there’s even an annual War Driving competition with results presented at the hacker convention, DEFCON every summer. The fourth and most recent competition was held June 12-19, 2004 .
The typical War Drive reveals a pattern of Wireless Access Points (WAPs) (see Figure 3).
Figure 3: A “WAP MAP” of 9 WAPs Revealing Individual Coverage Areas
(source: http://www.ittc.ku.edu/wlan/images_ittc_small.shtml)
This information is derived from a wireless detector or computer whose wireless card is operating in monitor (RFMON) mode. In the Jurassic period of War Driving (circa 2000), the war driver would have a front seat strewn with cables, antennae, GPS equipment, and a notebook computer. Now, this detection is usually done with a self-contained PDA, with analysis done offline on a full-screen computer. Figure 4 illustrates the process on a Windows CE-based PDA operating Air Magnet. As the graphic illustrates, the current scan is being performed on channel 6 for 802.11b traffic at 2.4370 GHz. The 2 WAPs detected are reported, along with their MAC addresses, names, and current signal strength. This information is collected and plotted, producing the WAP maps like those above.
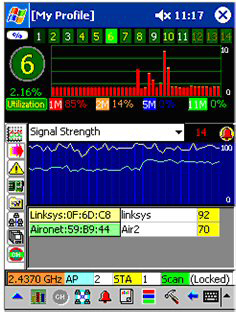
Figure 4: Wireless “sniffing” Palm Style with Air Magnet and a HP IPAQ Pocket PC
While this is a cursory overview, it gets to the essence of War Driving. I’ll expand on this in a subsequent column, Wireless Infidelities II: Air Hacking.
WARDRIVING LESSONS
In short, War Driving has taught us that wireless technology has opened the largest security hole in our computer networks since the advent of modems.
The data in Table 2 comes from the four WorldWide War Driving competitions.
| WWWD1(2002) (9374 WAPs) |
WWWD2(2002) |
WWWD3(2003) |
WWWD4(2004) |
|
Default SSID |
29.5% |
35.3% |
27.8% |
31.4% |
no WEP enabled |
69.9% |
72.0% |
67.7% |
61.6% |
Default SSID and no WEP enabled |
26.7% |
31.4% |
24.8% |
27.5% |
Table 2: WorldWide WarDrives (source: www.worldwidewardrive.org/)
By way of background, the Service Set ID (SSID) can be thought of as the “name” that is assigned to a WAP in “infrastructure mode”. This name is needed for clients to associate with it. Obviously, the first step toward of security is to avoid broadcasting the SSID to the world. The second step is to pick a name that isn’t the default set by the vendor. “Default SSID” reports the percentage of the WAPs that were discovered using the SSID that came “shrink wrapped” with the WAP hardware.
Wired Equivalent Privacy (WEP) is the anemic encryption technique used in the popular 802.11 protocols. Simply put, there’s little to recommend it as it fails virtually every reasonable standard for data integrity, confidentiality and authentication in both theory and implementation. While WEP will not withstand a serious attack from any would be intruder armed with free tools available on the Internet, it will slow down the attacker if properly configured, and will discourage neophytes who seek to authenticate with the WAP. The only thing worse than enabling WEP is not enabling WEP! The data in Table 1 shows that over 60% of the WAPS detected fail to have WEP enabled. In the wireless world, this is akin to leaving your wallet on the front porch for safekeeping.
The worst of all possible worlds is to not employ encryption and at the same time blast the name of your WAP to the entire neighborhood. 27.5% of the WAPS found have achieved that status.
Most alarming of all, the percentages do not seem to be changing much over time!
FINAL WORDS
The difference between wireless hacking and wireless monitoring is intent and moral orientation. From a technology perspective, they are two sides of the same coin. A similar point is made in an earlier column of mine on Internet Forensics (“On the Art of Internet Forensics, Communications of the ACM, 46:8 (2003)). The relevant skill sets of those who attempt to compromise network security and those who seek to protect them are for all practical purposes identical.
Therein lies the rub. The best of breed tools for wireless sniffing (Kismet for the *nix world, and Air Magnet for Windows) are used by both air jackers and wireless guardians, though toward different ends. This is a familiar story in network security – most of the products developed have benevolent and malevolent uses. (Although Dug Song’s switch flooder, Arpspoof, stretches this claim). The lesson to be learned from War Driving is that there is nothing inherent in the “sniffing” technology that encourages socially unacceptable or illegal behavior. The tools that the hacker might use to intercept organizational wireless traffic are the same tools that are used to harden the organizations’ wireless infrastructure.
The solution to the problem of misuse is awareness, both in terms of the capabilities of the tools and the uses toward which they’re put. Knowledge and vigilance are formidable adversaries of misuse. I’ve endeavored to contribute to the former in this column.
URL PEARLS
The de facto standard for War Dialing is THC-Scan 2.0 for Windows. It is available from The Hacker’s Choice (www.thc.org). One of many shareware Unix variants is Ward from Securiteam (www.securiteam.com/tools/6T0001P5QM.html).
War Chalking follows in the footsteps of Hobo tagging and Tramp Signing. A good source of the latter is www.worldpath.net/~minstrel/hobosign.htm. A popular War Chalking resource is www.blackbeltjones.com/warchalking/index2.html, The Google top hit, warchalking.org, seems to be non-functioning at this writing.
More information on the originator of the term War Driving, Peter Shipley, may be found on his Website, www.dis.org/shipley/. Details of his presentation at Defcon 9 in Las Vegas in July, 2001 may be found at www.defcon.org/html/defcon-9/defcon-9-speakers.html and in “Open WLANs – the early results of WarDriving” at www.dis.org/filez/openlans.pdf. For general access to the topic of War Driving in general, visit wardriving.com. A useful definition of War Driving is available on Paul McFedries’ Word Spy site (www.wordspy.com/words/wardriving.asp). The results of the four International War Driving competitions are documented at www.worldwidewardrive.org. By now everyone interested in information, computer and network security has heard of DEFCON (www.defcon.org).
Dug Song is one of the world’s premier “hackers.” He founded monkey.org some time ago, and through it has distributed a suite of very popular tools within both the white hat and black hat communities. Examples include dsniff (a network sniffing utility), fragroute (a generic packet fragmenting tool), the switch state table flooder macof discussed above, and dozens of other tools. In the past few years he has restricted access to some of these resources – see www.linuxsecurity.com/articles/cryptography_article-3624.html, though most remain easy to find via Web search.
WAP mapping is an interesting multimedia exercise in its own right. Figure 3 was produced by the University of Kansas ’ Wireless Network Visualization Project (www.ittc.ku.edu/wlan/). The coverage maps are particularly revealing from the point of view of wireless leakage. A more general source of “cybermaps” is the Atlas of Cyberspace site at www.cybergeography.org/atlas/.
At this writing, the best wireless detectors that I know of are Kismet (www.kismetwireless.net) for *nix and Air Magnet (www.airmagnet.com) for Windows.
A useful guide to 802.11 wireless technology is Matthew Gast’s 802.11 Wireless Networks: The Definitive Guide, O’Reilly & Associates, Sebastopol (2002).
SIDEBAR
More on Alternate Data Streams.
We were pleased to get feedback from so many of you on our December column on Alternate Data Streams. We’re still getting feedback eight months after the issue appeared in print, which is unusual for columns. We’re also pleased that most of the responses were sympathetic to our idea that the negative publicity surrounding Window’s ADSs is undeserved. If Microsoft is to be faulted, it’s for not releasing enough technical documentation to ensure that ADSs can be deployed effectively, efficiently, and securely.
As many of you noted, there was an error in our reporting on the Mac OS X lineage. We incorrectly reported that Mac OS X was built on a Linux kernel. It is actually built on Mach micro kernel derived from FreeBSD. OS X using Apple's HFS+ file system still uses file forks; the alternative UFS (Unix File System) uses .rsrc files instead.
In addition, there was a nasty typo. In the third paragraph, “non-monotonic” should be replaced by “non-monolithic.” Our thanks to Tom Goodale for pointing this one out.