 accesses since November 29, 2013
accesses since November 29, 2013
 copyright notice
copyright notice link to published version: IEEE Computer, January, 2014
link to published version: IEEE Computer, January, 2014
 accesses since November 29, 2013
accesses since November 29, 2013
How did we get to the current state of privacy abuse in our current surveillance society? To start, elected representatives have become the lapdogs for business interests that derive benefit from surveillance economics. We also enjoy the collateral benefits of the technologies used in surveillance: cameras for home protection, GPS for navigation, RFID cards for everything from access control to vehicle telematics to heart pacemakers, OnStar for emergencies (and eavesdropping), the world wide web for e_commerce, etc. Along the way, it never occurred to most of us that the technology that allowed us to call for help in an automobile accident might also be used to record personal meetings in a car and use those recordings to convict people of crimes. From the technology perspective, you can’t have one without the other. It’s a packaged deal.
But most of all, we're a distracted society. Distracted by television, radio, advertising, web surfing, social networking, texting, a potpourri of digital distractions. As Neil Postman put it, we're “amusing ourselves to death,” and that has led us to a Huxleyan (vs. Orwellian) dystopia where talking heads and visual images distract us from issues of genuine importance. In Modernity and the Holocaust , sociologist Zygmund Bauman said that "rational people will quietly, meekly go into gas chambers if only you allow them to believe that they're bathrooms." So, willingly we digital denizens marched to our futures where the price for privacy was digital death. We did this to ourselves by behaving rationally and passively. But as Bauman further noted “The rationality of the ruled is always the weapon of the rulers.” In this case, the “rulers” are the political and financial neoliberal elite who have vested interests in their own information monopolies.
We bear this responsibility whenever we provide personal information to geneology and social networking sites, credit card companies, online e_commerce, health care professionals, schools, religious organizations, and so on. Of course, there is a minimal amount of information that is required to sustain social interaction and commerce. But as a society we maxed out on that generations ago. Everyone who uses the cloud, Facebook, and smart phones while not using anonymization and encryption, is part of the problem.
So, where do we go from here? I offer here the poor person's substitute. It won't fix your privacy problems, but it's better than nothing.
Ten years ago I launched “Better-than-Nothing-Security-Practices” ( http://www.berghel.net/btnsp/btnsp.php in a desperate attempt to satisfy some basic security needs for clients and audiences. Nowhere near the depth, breadth and quality of SANS training - the single most important resource for security training in the world (sans.org) – it had the distinct advantage of being free. I'm comfortable in speculating that it lived up to its name and was not overpriced.
Ten years have elapsed and the world's digital concerns have shifted from mostly security to a balance between security and privacy. Edward Snowden's greatest contribution may be that he, more than any other individual, added fuel to the global debate on privacy. Ten years ago, I devoted attention to publicize security threats from hackers and criminals. These days I'm devoting considerable effort to educate people about privacy threats from government and industry. Although the wardrobe and beverage choices of the players may have changed, the abuse of the electorate remained constant.
This is the first installment of my Better-than-Nothing-Privacy-Practices series. In this episode, I'll focus on two common tools: browsers and cell phones – specifically, Mozilla Firefox v. 24.0 and Android v. 2.3.3, two tools that I rely on heavily. Our goal is to raise the bar a little for those digital demons who might wish to violate our privacy.
From the version numbers it's clear that I don't update my Android but do keep Firefox current. This is due to very different levels of trust I have in the companies and products involved.
The initial configuration of Firefox is critical to prepare for privacy enhancements of add-ons that I'll return to in a few paragraphs. I offer these few observations for those who are not in the habit of tweaking their browser security and privacy settings just to set the stage. For more thorough analyses readers are directed to the wealth of online resources.
We begin with the Mozilla privacy panel (menubar>options>privacy tab). I recommend for your consideration checking “tell sites that I do not want to be tracked” (the so-called Do Not Track option). Under custom settings for history, I recommend checking both “always use private browsing mode” and “accept cookies from sites”. However, for “accept third-party cookies” the better option is Never. Set “when using the location bar suggest” equal to Nothing. Using the custom settings option in this way automatically clears the history when Firefox closes (a byproduct of private browsing mode). It is always wise to click on “Show Cookies” now and again to inspect for cookie crumbs. Actually, occasionally force my browser to manually discard cookies and other cache items like scripts (e.g. <ga.js>) to minimize the risk of packet injection. A delightful little add-on called Empty Cache Button works well for this. It's amazing to hard it is to keep the net snoops' mitts off our cache.
Now let's see what we have accomplished. First, the Do Not Track option falls under the category of “gratuitous act of defiance for optimists” (see this column, September, 2013). DNT is an accepted IETF HTTP header field, but (and here's the rub), it is not a “core” header field and hence not required for IETF compliancy. Simply put, servers and network appliances may ignore without penalty and remain in conformance with standards. So why do it? Because some Web servers are respectful of the user's privacy, and in that case DNT works. Many of us continue to call for rigid enforcement of DNT and someday this may pay off. (I'm not holding my breath now that corporate America is the de facto regulator of the Internet.) In any case, after a reboot of Firefox these settings should produce no recorded history and minimal crumbs.
The “History” and “Location Bar” recommendations limit the amount of “browser guano” left on the computer. Firefox originally included history and location bar options to limit the recovery of this information from public or shared computers. However, in the age of warrantless wiretaps, extra-judicial detention, and penetration of journalist's shield laws, it's wise to consider preventing this information from getting through in the first place. Any minimal inconvenience is more than offset by an increased protection against the computer activity mining performed by government law enforcement, private surveillance merchants, and corporate information harvesters. Needless to say this will undercut the use of your “Awesome Bar.”
The rationale for this sort of privacy configuration minimizes exposure of access to user behavior by prying eyes, legal and not. I emphasize “minimize” here because browser developers are less than transparent these days on where they hide this stuff. Earlier versions of Firefox, for example, allowed the user to specify the location of the browser cache. That made monitoring and clean-up straightforward. Now, Firefox buries sundry metadata and browser guano as history, bookmarks, cookies, configuration settings, passwords, autocomplete histories, etc. in a special profile folder ( %APPDATA%\Mozilla\Firefox\Profiles\ ) (in this case on Windows computers), much in encoded or encrypted form, so there's no easy way to find it and inspect it. Mozilla claims that having this profile isolated from the application is a feature, because the data integrity isn't dependent on the stability of Firefox. Baloney. This is just another developer's way of restricting user behavior for their own convenience and selfish purposes. Making the eradication of browser guano a hassle for the user serves the interests of myopic software developers who believe that their vision of computer use trumps the privacy interests of the customer. For those interested in more detail, I have discussed the recovery of such residue under the rubric of BRAP (BRowser and Applications) F orensics elsewhere ( http://www.berghel.net/col-edit/digital_village/jun-08/dv_6-08.pdf ).
Now on to the security settings (security tab). Check “Warn me when sites try to install add-ons”, “Block reported attack sites,” and “Block reported web forgeries.” I recommend avoiding both password options. As a general guideline, browsers are not optimal tools for password management. There are other configuration settings that enhance privacy and security to be sure, but these few changes are enough to move us forward to the real breakthrough in personal privacy and security for browsers: the add-ons. Where the 1990's were characterized by the browser wars (see my 1998 perspective at http://www.berghel.net/col-edit/digital_village/oct-98/dv_10-98.pdf ) , we've now entered the era of add-on skirmishes.
To start, I'm going to recommend two add-ons unreservedly – both offered though the Electronic Frontier Foundation – for many years a leading voice behind the protection of civil liberties in cyberspace.
First, NoScript. This product is a dream come true for privacy zealots – a customizable real-time, interactive script blocker that is free. What a deal.
NoScript is designed to work seamlessly with scripting environments that operate with the more popular secure-sandbox-model virtual machines like Java, JavaScript, and Flash. I've had no problem with Adobe Reader, Acrobat, Silverlight, and Windows Media Player either. NoScript uses several innovations to get you around the problem where blocking the script renders the Web page unreadable. NoScript uses script surrogates that function like the script embedded in the page for the most part, preserving usability, breaking nothing critical while disabling nastiness. Script surrogates deal with page scripts of many ilk, including distracting “pop-unders” (aka on-click pop ups). NoScript also is effective at blocking cross-site scripting attacks and IFRAMEs to prevent clickjacking. It also has HTTPS forcing as an option (which I don't use - see below). But even if NoScript breaks something, the configuration (NoScript Icon>Options) allows you to tailor it to suit your need. However, you can also configure on-the-fly with NoScript by simply selecting which of the scripts you want to run.
One of the best features of NoScript is its compatibility with other add-ons (and there are many good ones available). The latest version is 2.6.8.5 see http://noscript.net . I should mention that silent running with NoScript comes with a penality – you will have to go one extra step to temporarily enable scripts (individually or as a group) on script hog sites, but that will give you the opportunity to reflect on whether the visited sight is worthy of your interest after all. If you're interested in protecting your online privacy, this minor irritation is minor compared to the risk avoided.
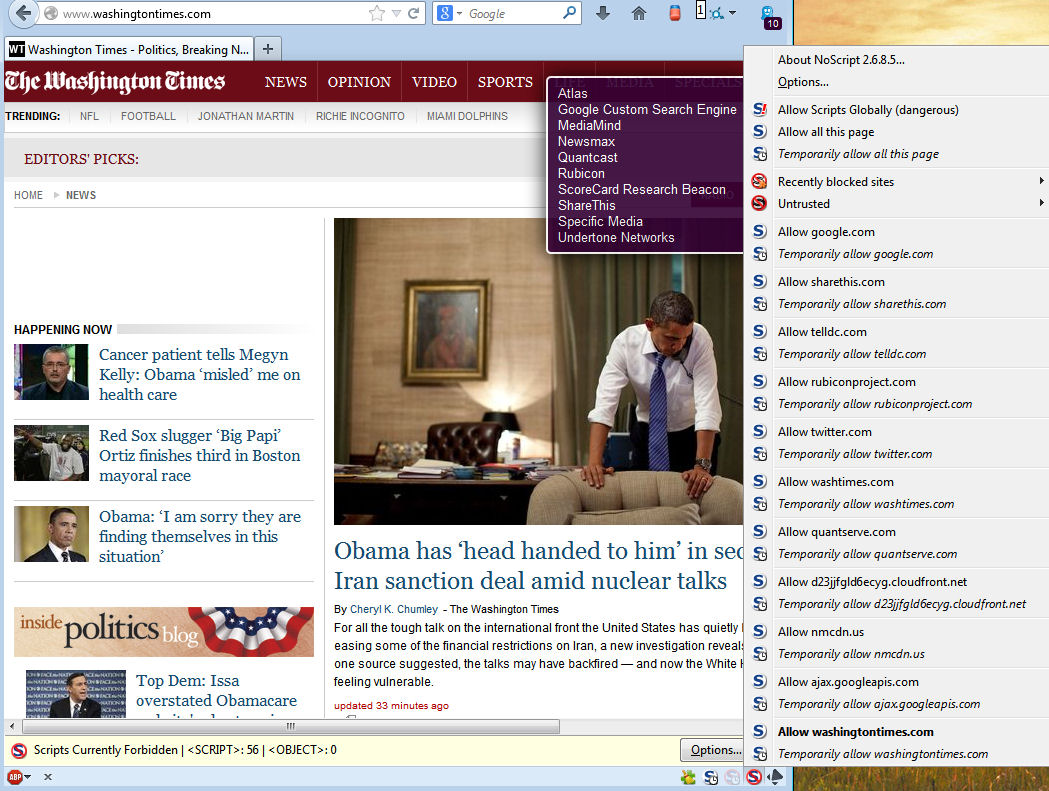
Figure 1a: NoScript Control NoScript Contol: the smaller box indicates which scripts are set to run. The panel allows the user to select which scripts if any to run for this page. In this case, I don’t need to enable any of them to read the articles.
Figure 1b
HTTPS Everywhere is a sister add-on from EFF. This add-on only does one thing: it forces a TLS/SSL HTPPS connection if is available on the server. It does this by means of the HTTP Strict Transport Security protocol (HSTS; RFC 6797). Of course, HTTPS is always preferable to HTTP where privacy is concerned, but until HSTS the user had no way of knowing whether it was available. In addition, as Moxie Marlinspike showed in 2009, basic HTTPS may be vulnerable to a “SSL-stripping man-in-the-middle” attack, where a hacker could convert a secure HTTPS connection into an insecure HTTP connection without the user's awareness. Both the need of defaulting to HTTPS when possible, and preventing the Marlinspike hack are dealt with in HTTPS Everywhere. In addition, EFF builds in the SSL Observatory that monitors the use of HTPPS certificates on the Internet and provides warnings of possible attacks. While NoScript also has HTTPS-forcing built in, its list-oriented configuration is more primitive and not as convenient. See https://www.eff.org/https-everywhere. The current version for Firefox is 3.4.2.xpi ( https://www.eff.org/https-everywhere/ ).
There are far too many good browser add-ons to describe in one setting, so stay tuned to the Out-of-Band Computer channel for updates. Remember that caveat emptor applies with add-ons as the code typically isn't validated by trusted 3 rd parties. For that reason, I recommend staying with add-ons that are written by organizations you trust.
Let's face it, the TELCOs have been illegally sharing our information with the government (and who knows who else) at least as far back as the 1919 when Herbert Yardley formed his Black Chamber spy group after World War I. The big Telcos of the day, Western Union Telegraph Company, Postal Telegraph, All-American Cable Company were then, as the big Telcos are now, eavesdropping on U.S. citizens illegally on behalf of the government. The big difference is that these days the Telcos spy with immunity from prosecution.
So the modern Telcos aren't doing anything particularly unusual for their industry, and neither is the U.S. Government's use of the Telcos to eavesdrop on U.S. citizens. (cf. Operation Shamrock, Operation Minaret, COINTELPRO). There have always been rooms like 641A somewhere. The recent twists are the Narus and Verint intercept suites and the optical fiber they work with. The stress testing of the Bill of Rights remains the same.
The same applies to WiFi – especially metropolitan area networks. Alternative online magazine The Stranger recently exposed the Seattle Police Department's use of their infamous “white boxes” to intercept and store in a database such information as IP addresses, device type, applications running on the device, and location history ( http://www.thestranger.com/seattle/you-are-a-rogue-device/Content?oid=18143845 ). Since this project was funded by the U.S. government (Department of Homeland Security) it's unlikely that it's unique among metropolitan areas. SPD apparently denied activating the white boxes until David Ham of Seattle's KIRO-7 News team asked why the wireless access point names were identified by smart phones ( http://rt.com/usa/seattle-mesh-network-disabled-676/ ). Another public deception over surveillance. Imagine that.
So, Seattle residents (and all you other white boxers out there), here are a few modest suggestions. But first a few caveats: (1) My remarks only apply to Android 2.3.3 on Casio 771/Verizon smart phones. The reader will have to extrapolate from there. (2) The only effective countermeasure to undesired business and government eavesdropping and surveillance of cell phones is to “jailbreak” it to gain root privileges and from root block all of the intrusive functionality from the carrier, Google, and the applications developers. I should note that the law in this area is magnificent in its misorder, and continuously in flux.
To illustrate, the firmware in your smartphone is covered by the Digital Millennium Copyright Act (DMCA) which is interpreted every few years by the Librarian of Congress. In his most recent 2012 ruling, he has opined that jail breaking your smartphone will remain legal until 2015, but that unlocking a smartphone is illegal if it's made after December 31, 2012. ( http://arstechnica.com/tech-policy/2010/07/apple-loses-big-in-drm-ruling-jailbreaks-are-fair-use/ ). Note that under his penultimate opinion, the opposite was the case. Without rooting your phone, the Telco can do/undo anything that you undo/do if they choose, and if you do root your phone the Telco may develop an attitude and threaten to discontinue warranty service. So, at this writing, I'll take a swerve around jail breaking and unlocking issues leaving them to you and your attorney.
The security and privacy threats presented by smartphones and cell phones are real and should be taken seriously ( http://blogs.computerworld.com/android/22806/google-knows-nearly-every-wi-fi-password-world ; http://www.zdnet.com/millions-of-android-users-vulnerable-to-security-threats-say-feds-7000019845/ ). With these few caveats in mind, we offer some privacy tactics for your consideration.
I'll organize these suggestions by menu item. First, the Telcos and their federal 3-letter agency partners have no business knowing where you are without your permission. So, let's shut off GPS services until we need them.
Settings > Location & Security
- VZW Location services (uncheck)
- Standalone GPS Services (uncheck)
- Google Location Services (uncheck)
Bear in mind that GPS 911 tracking will not be available with these services disabled, so if you’re in a fix you won’t be able to tell the 911 operator to “come find you” – you’ll either have to tell them where you are or turn the GPS services back on.
Settings > Privacy
- Back up my data to Google servers (uncheck)
Give me a break. I wouldn’t trust Google with my dirty laundry much less my passwords (cf http://blogs.computerworld.com/android/22806/google-knows-nearly-every-wi-fi-password-world). We continue,
Settings > Wireless & Networks > Mobile Networks >
- Data Enabled (uncheck)
- Global Data Roaming Access
- Deny data roaming access Access (or “Allow access only for this trip)
- Wi-Fi (uncheck/off until needed)
- Bluetooth (uncheck/off until needed)
Settings > Accounts & Synch
- Background data (uncheck/off unless needed)
- Backup assistant (uncheck/off unless needed)
- Disable Synch for all accounts
Settings > Applications
- Allow installation of non-market apps/unknown sources (uncheck/off)
Settings > Security
- Encrypt both device memory and SD card with different, long complex passwords that is different from the boot password
And when installing an application, carefully read the entire list of permissions required for the application. If the app seeks permissions for camera, microphone, etc. that you don't think is reasonable, don't install it. Remember, the Telcos operate under the caveat emptor rubric (and immunity!).
So there you have it. You've turned your smartphone into a paperweight. But it's a Constitutionally-friendly, libertarian-and-privacy-pleasing paperweight that can make phone calls. That's not bad for a phone. And, of course, you can always turn these features back on and undo everything.
So, this is the first installment of my new Better-than-Nothing- Privacy-Practices suite. Let me know what you think. This primer barely scratches the surface, but it's…. – well, you know.
I would be remiss if I failed to again emphasize the obvious: the use of smart phones and the Web are, in and of themselves, invitations to privacy abuse (think Seattle!). The same applies to the use of social networking services like Facebook, Google+, Twitter, Linkedin, to name but a few, and storing data on a cloud service. As Nicholas Weaver puts it, the Government has Weaponized the Internet ( http://www.wired.com/opinion/2013/11/this-is-how-the-internet-backbone-has-been-turned-into-a-weapon ), and unfortunately there's a host of private cyber-mercenaries like ManTech, the Gamma Group, and Stratfor that are also in the mix (see, http://www.washingtonpost.com/blogs/the-switch/wp/2013/11/04/yes-there-actually-is-a-huge-difference-between-government-and-corporate-surveillance/?tid=up_next .)
But then the same may be said of the use of lower-tech credit and debit cards. Bankers, credit card vendors, and law enforcement agencies are all in agreement on one point: cash is the enemy of Big Brother.
Limiting use of such technology platforms and services is not a product of technophobia or neo-Ludditism, but rather a defensive reaction to the rise of this modern “digital heel” that is used to control and manipulate the populace. These technologies are the grist for Orwellian and Huxleyan mills.
Those who persist at using privacy-revealing technologies and operating browsers in unsafe modes will probably not derive much benefit from the suggestions given here. But for the rest, this is a start. Those of us in the computing disciplines have been aware of security/privacy vs. usability trade-offs throughout our professional lives. Some more aware than others. What is new to this millennia is that governments have taken the leadership position in privacy and security abuses, from Stuxnet to tapping Angela Merkel's cell phones. Hopefully, we'll all soon come to appreciate that the price for personal privacy is eternal vigilance!