 accesses since October 1, 2005
accesses since October 1, 2005
 copyright notice
copyright notice
 accesses since October 1, 2005
accesses since October 1, 2005
Hal Berghel
"What is this thing called malware?
What denizens of darkness loom behind this door of doom,
that future generations will not know the wily hacker's haunt?"
I came up with this myself. Ok, I'm no William Butler Yeats, but Jeannie pays me an extra $2.50 whenever I wax eloquent. I'm hoping that this is worth at least $1.75. I'm saving up for a box of cisco gummy worms - hard and crunchy on the outside, but soft and chewy on the inside.
But I digress. The present topic is malware. The fact of the matter is that when it comes to malware, we ain't seen nothin' yet. Do you want to get really, really scared? Read on.
Let's begin by discussing a category of software I'll call "riskware." Riskware may be divided according to the nature of the risk: privacy, security, etc. Examples of privacy riskware include adware, spyware, trackware, and the like. Examples of security riskware include worms, viruses, backdoors, Trojan horses, etc. alone or in combination. The popular term for security riskware is malware. Malware falls within the scope of computer and network vulnerabilities.
The point of this bit of lexicography is that one category of riskware - malware - is undergoing a transformation. What is more, this transformation has pandemic potential. Malware may be the digital analog to AIDS and the bird flu epidemic.
First, let's do a quick aerial survey of the deployment of malware in 2005 from a hacker's perspective. A typical scenario might go something like this. A wily hacker begins with an objective: compromising the security safeguards for military computers at a certain location, copying trade secret files from a server farm in a domestic company, altering selected player card records at a casino, etc. Next, a strategy unfolds. A vanilla strategy might look something like the following:
I've included some names of actual software that is used for these purposes in parentheses for you to Google over. A quick inspection will show that some of these tools are downright scary!
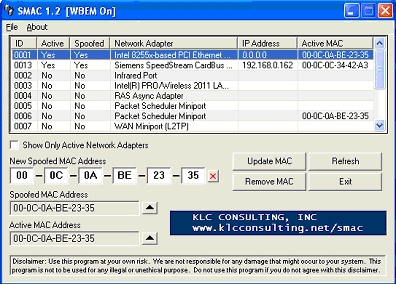
You may have heard that one of the lines of defense from firewalls to WiFi is "MAC ID Filtering." This is a technique whereby connection between computers or network appliances is only allowed if the MAC addresses of the endpoints match entries in the internal state table. It is not unusual to hear IT specialists refer to MAC ID filtering as an added layer of security. In fact, nothing could be further from the truth. Look at the figure below of SMAC 1.2 the Windows-based MAC ID spoofer. Note the easy-to-use interface, especially the text entry areas for the bogus MAC ID that the user can enter. The plain fact is that with SMAC, the user is 12 keystrokes and a mouse click away from spoofing any MAC ID whatsoever! Consider that when your CSO touts MAC ID filtering as the panacea for overcoming the vulnerabilities in your WiFi infrastructure.
So we already admit that we're vulnerable, and we can easily confirm that there are scary tools out there for the hacker, cybercriminal, or cyberterrorist. If that's not bad enough, the arsenal of malware is undergoing a transformation that makes it far more dangerous for us.
Today, a hacker that goes through something like the strategy above, the result is what we in the security biz call an "event." We'll assume that our event is some sort of program that exploits a vulnerability in our enterprise network infrastructure. Today's vulnerabilities may be classified by:
Identifying signatures is the closest to most of us, because they're used by our firewalls. When our anti-virus vendor pushes out the weekly updates, they're pushing out signature records for the vulnerabilities discovered that week. Suppose that there weren't any identifying signatures. Yep, that's the transformation that malware is undergoing.
The leading incident handlers are seeing new types of exploits that behave very differently than those of the Jurassic period (i.e., last year). The best way to explain these exploits is with respect to the list above. The new generation of malware is targeting multiple systems at the same time, with multiple warheads, with different, parallel deployment tactics, and doing so before we can identify the signatures.
Some of this malware has already been observed. The Ramen worm had three different exploits. One of the recent versions of Nimda had a dozen. IIS/Sadmind targeted Windows and Solaris operating systems. The so-called "Zero-day" exploits derive their name from the fact that the first appearance of the worm is in and of itself the first exploit. The days when we have a month's lead time between the issuance of Microsoft's patch or hotfix and the first appearance of the exploit are coming to an end. (As an aside, both W32/Blaster and the SoBig exploits were both launched a month after Microsoft announced the patch. And even with a month's lead time, we still accumulated an estimated $50 billion in lost revenue and productivity.
Two new categories of malware also prevent easy identification and classification - and hence signatures. Polymorphic worms change their appearance as they propagate. When the exploit hits my network it looks different than when it hits yours the same day. Thus, even if the security vendors update their records with the signature of the code that hit me, it won't help you. Metamorphic worms not only change their appearance as they propagate, they also change their functionality. Future malware will be "breeders" not "warriors." That makes them all the more dangerous, for there won't be anything to detect as they propagate until it's too late.
Malware's second coming is the age of binary pandemic: soon to be at an enterprise infrastructure near you.